With the growing number of security threats to electric power utilities worldwide, in Japan, the requirements for cybersecurity measures on power control systems now are subject to legislation, which has resulted in an increase in efforts to maintain system security. In 2016, security guidelines for electric power utilities were published in a 32-page document, “Power Control System Security Guidelines (JESC Z0004),” which now forms part of the Japanese regulations. All Japanese utilities must follow the national guidelines, designed to maintain reliable and secure operation of power control and information systems.
Using the International Organization for Standardization’s ISO27001:2013 and ISO27002:2013 information security management standards as a reference, Japan’s guidelines provide a brief description of items that require security measures, including administrative, technical and physical requirements. Unlike the North American Electric Reliability Corporation’s Critical Infrastructure Protection standards, Japan’s guidelines do not specify how to provide security. Rather, Japanese utilities can select the most appropriate security measures for their power control and information systems in the most cost-effective way.
TEPCO Power Grid Inc. (TEPCO PG) and Kyushu Electric Power Co. Inc. (Kyushu EPCO) are two such utilities that have developed unique security strategies, in compliance with Japan’s guidelines, to meet their specific needs.
System Characteristics
A utility should be completely aware of the typical characteristics of operational technology (OT) systems when establishing security strategies for power control systems. Typical characteristics of power control systems are as follows:
- Load dispatch, transmission, distribution and substation management power control systems are so specialized and sophisticated that each system is managed independently by various departments in the utility.
- Endangerment to safety and disruption of power supply are critical risks. Security controls must never degrade the safety and availability of power supply.
- Security patch management is technically difficult because each power control system is isolated from other networks. Therefore, if a security patch is deployed, secure outside connectivity should be provided.
- Power control systems have a large variety and quantity of system components over a wide geographical area. Unlike information technology (IT) systems, OT systems and network components are widely distributed. Because of this, asset management, system configuration management, physical security management, security threat analysis and detecting cyberattacks can be much more difficult.
- A primary target of attack on an OT system could result in an operation malfunction or physical damage but not necessarily confidential data being stolen, as is the case with IT systems. However, these problems can occur often because of accidental equipment failure or maintenance work. Power control system security monitoring must quickly identify whether the problem is the result of a failure, maintenance or a security incident.
- System operation expertise is vital for security response, as it is important to detect suspicious behavior in operations and transactions.
Security Strategies
Strong security strategies for power control require a security governing structure, such as a centralized computer security incident response team comprising power control system experts who can differentiate an operational error from an accidental failure or a cyberattack.
The development of a common security system infrastructure can introduce risks, as the interconnection of various systems has the potential to increase vulnerability and invasion routes. As power control systems vary and are large and geographically widespread, keeping them secure is a challenging task. Fortunately, the risks associated with using IT security products for power control systems have been eliminated now that OT security products are commercially available.
TEPCO PG’s Strategy
TEPCO PG is a large Japanese electric utility with many power control systems, from supply and demand control to energy transmission and distribution, in addition to its systems for data acquisition and business processing. After the Japanese power control system security guidelines were published, TEPCO PG implemented a number of changes in the way it manages security, including establishing a security governing organization, setting in-house security rules, implementing IT and OT integrated security monitoring, developing skill sets and creating cyberattack simulation exercises.
Security Organization
Previously, TEPCO PG had no specialized organization to govern and monitor the security measures in an integrated manner. Security efforts were the responsibility of individual departments. The utility now has two security organizations under the chief information security officer: a security incident response team (SIRT) and the security operations center (SOC).
The establishment of SIRT and SOC has enabled the steady implementation of actions, such as the development of in-house security rules, implementation of the plan-do-check-act (PDCA) cycle of the security plan and development of a response flow in the event of a security incident. For instance, existing power control systems have been checked for conformity to the power control system security guidelines, and penetration tests and detailed risk analysis have been regularly executed for important systems.
With regard to cyberattacks, it is beneficial to share security information among government agencies, the power industry, other infrastructure industries and security vendors. Japanese industry organizations already are involved in these efforts.
In-House Rules
TEPCO PG has made considerable changes to its in-house security rules. The importance levels of power control systems as well as security controls according to these importance levels are documented. The security controls now include technical measures, such as anti-malware, vulnerability information management and log monitoring, as well as physical measures, such as external storage device management, camera monitoring and access control.
Integrated Monitoring
All integrated security monitoring is now conducted by the SOC, which monitors all anomalies detected by several types of security devices. The SOC also monitors power control system logs. In order to handle those logs effectively and efficiently, designing optimal security log feature is one of the key technical issues for future considerations.
Security Skills
While it is important to assign team members with sophisticated security skills to manage the SIRT and SOC, in the event of a security incident, appropriate assessment of the situation may not be possible without knowledge of how the power control systems operate. Furthermore, it is necessary to understand the log messages that are specialized for each system and to accumulate the knowledge and ability to identify the information necessary for security. TEPCO PG develops the security skills of its in-house power control systems professionals and supplements this with external security experts to handle its detailed security tasks.
However, the level of security skills necessary for security professionals in utilities is still under discussion. For example, TEPCO PG is not certain its security professionals require skills that would enable them to achieve excellent results at a hacking contest or disassemble hardware and find vulnerable code. However, sophisticated IT security skills certainly are necessary to detect invasions at the reconnaissance steps of an attack and develop strong anti-invasion tools. TEPCO PG currently is trying to develop a skill map using the U.S. National Institute of Standards and Technology’s National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework as a reference.
Simulation Exercises
Many cyberattacks are observed daily in the IT world, but normally this is not the case for power control systems. TEPCO PG’s SOC sometimes detects security alarms, but the majority are not a true security incident. Therefore, the utility has found regular cyberattack simulation exercises are a good way to prepare for real attacks. Some of the simulations are conducted without giving team members advance notice.
Team members from a wide range of functional areas across the enterprise participate in the simulations, including leadership, SIRT, SOC, system operators and public relations, depending on the scenario. By conducting and designing various simulation exercises, the inherent problems of current response flow can be identified.
Kyushu EPCO’s Strategy
Another Japanese utility, Kyushu EPCO provides power to seven prefectures, or subregions, of Japan. Much like TEPCO PG, this utility also changed its organization structure. Kyushu EPCO established a dedicated organization to monitor its information systems.
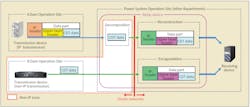
Information necessary to the operation of its power system is transmitted from hydro plant dam operation sites to the power system operation site. This information includes the water volume discharged by the power generation dams and their water level as well as the updating of the dam management systems.
The utility has been shifting its communication method from the conventional cyclic data transfer (CDT) method to the internet protocol (IP) method. The CDT systems require relatively expensive dedicated transmission devices. With the IP method, cost is reduced because the network can be constructed using general-purpose devices. If the IP network already is in place, the cost for construction can be even less. Converting the communication method to the IP network enables usage of the existing IP network and general-purpose network equipment when constructing new networks, resulting in a reduction of the construction costs of the transmission system.
On the other hand, IP migration creates the need to consider defense against cyberattacks, such as unauthorized accesses and intrusions of malwares into the network. Specifically, the propagation of cyberattacks occurring in certain networks to the power control systems connected to the network can cause serious problems, such as the trouble to supply power to customers.
Furthermore, the dam operation site and power system operation site are separate networks because these two sites are divided internally at Kyushu EPCO. Therefore, the network security measures between the dam operation site and power system operation site are important issues in the IP migration of the dam management system.
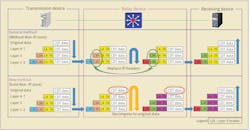
Kyushu EPCO adopted a method to decompose the IP format to the original data and reconstruct the data to a new IP format using a relay device installed at the boundary between the different networks. This method makes it possible to separate the different networks logically, preventing security incidents in other networks from spreading to the connected network.
As a result of adopting this method, the utility remodeled the relay devices to translate CDT format and IP format to the same IP format. The data is transmitted to the receiving device at the power system operation site. General transmission methods of IP format data replace IP headers with relay devices, such as routers. In this case, different IP networks are connected by the relay devices.
The relay devices are used to decompose the IP format data received from the transmitting device to the CDT format data. The CDT format data passes into the internal bus, and the new IP format data is reconstructed from the CDT format data. Finally, the IP format data is transmitted to the receiving device. As a result, the data can be exchanged between different networks while being separated as IP networks.
In accordance with Japan’s control system security guidelines, a proprietary non-IP is adopted at the connection point between different networks. Hence, Kyushu EPCO has ensured its IP network security complies with the country’s security guidelines.
Machine Learning
The utility collects information on the performance of all its servers and communication devices at regular intervals to monitor its information systems. For important information, thresholds are set and any collected data that exceeds these thresholds is detected and recorded as an anomaly.
With the aim of improving the level of operation in the future, Kyushu EPCO has conducted verification to determine the feasibility of early detection and prevention of failures by monitoring using machine learning.
Failure Monitoring
The current anomaly detection mechanism is designed to issue an alert when specific software goes down or the load applied to a server exceeds the preset threshold. However, in some cases, this mechanism is unable to detect failures only by means such as threshold monitoring and alive monitoring, resulting in a delayed response.
To address this problem, failure monitoring using machine learning constructs a model, by analyzing data characteristics based on the data acquired during the normal state, to detect deviations from the model. Failure monitoring enables the utility to detect and perform predictive analysis of anomalies that cannot be detected by threshold monitoring.
Anomaly Detection Process
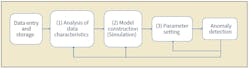
To achieve anomaly detection using machine learning, a process comprising data entry and analysis, model construction and parameter setting is performed according to the following flow process:
- Data stored in the past is used to analyze whether or not target data has characteristics (periodicity, normality and correlation) that can be used for the detection of anomalies.
- Characteristics identified by the analysis are used to select an algorithm for determination of whether the data is normal or abnormal.
- Parameters of the selected algorithm are set to increase the accuracy of anomaly determination.
Verification
Verification is conducted to determine whether the failure monitoring system, using machine learning, enables early detection when communication device failures occur. If the results of the analysis of data characteristics reveal that the traffic data from a communication acquired during the learning period has period characteristics, a model is constructed based on those period characteristics, thereby enabling the detection of the collapse of the period characteristics immediately before a failure occurs.
Although failures were detected during the verification process, the failure detection took place immediately before the failure occurred; hence, it failed to achieve predictive detection. In the future, the algorithm parameters will need to be reviewed so failure predictions can be detected earlier.
Refining Security Strategies
TEPCO PG and Kyushu EPCO are examples of utilities that have developed unique security strategies specific to their operational needs. The utilities will continue to refine their strategies to protect against the growing number of security threats while ensuring compliance with Japan’s guidelines.